Tag: network security

Avoiding proxy detection by anti-bot systems
Navigating the Labyrinth: Avoiding Proxy Detection by Anti-Bot Systems In an era where digital interaction...

An In-Depth Analysis of TLS/SSL Proxy Errors Related to Proxy Usage
In an era defined by heightened security measures and the relentless pursuit of privacy, the...

Proxy Fingerprinting Detection: An In-Depth Analysis
In an era where digital privacy and security are paramount, the use of proxies has...

An In-Depth Analysis of IP Bans and Blacklists Related to Proxy Usage
In the ever-evolving landscape of the internet, the use of proxies has become a double-edged...

DNS leaks with proxies
Understanding DNS Leaks in Proxy Usage: An Analytical Perspective In a world increasingly characterized by...

An In-Depth Analysis of SOCKS5 Proxy Connection Issues
In the realm of internet privacy and security, the importance of proxy servers cannot be...

Proxy testing and verification
In-Depth Analysis of Proxy Testing and Verification: Navigating the Complex Landscape of Proxy Usage In...

Residential vs. Datacenter Proxy Problems: An In-Depth Analysis
In the digital age, the art of navigating online spaces has become both a necessity...
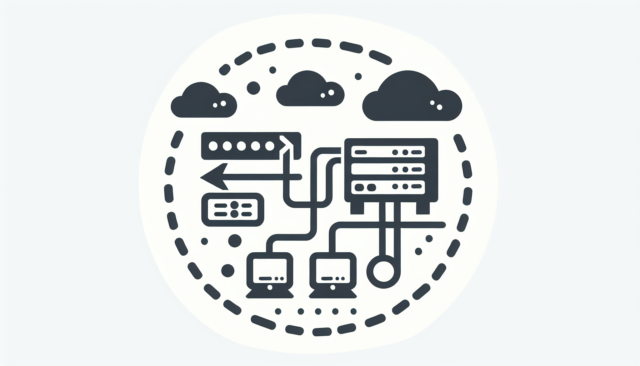
How Do Proxy Servers Work?
The Intricate Mechanisms of Proxy Servers: Performance, Anonymity, and Security In the vast digital landscape,...

Reverse DNS Lookup
Understanding Reverse DNS Lookup in the Context of Proxy Performance, Anonymity, and Security In the...

TLS/SSL Encryption
Understanding the Impact of TLS/SSL Encryption on Proxy Performance, Anonymity, and Security In the digital...

Firewall
Impact of Firewall on Proxy Performance, Anonymity, and Security Firewalls play a crucial role in...

Subnet
Understanding Subnet and Its Impact on Proxy Performance, Anonymity, and Security What is Subnetting? Subnetting...